PythonPro #18: Gemini Advanced Talks Python, Google Sheets Traps and Tricks, Duck Typing, Memray, & Secure App Development
Bite-sized actionable content, practical tutorials, and resources for Python Programmers and Data Scientists
Welcome to a brand new issue of PythonPro!
In today’s Expert Insight we bring you an excerpt from the recently published book,
Web App Development Made Simple with Streamlit, that teaches you the applications and security benefits of SHA-256 (a secure cryptographic hash function), essential for secure web application development.
News Highlights: Gemini Advanced introduces a Python Interpreter for $20/month for code execution, and Pydantic 2.6.3 updates documentation and fixes a schema bug..
Here are my top 5 picks from our learning resources today:
Building an E-commerce Product Recommendation System with OpenAI Embeddings in Python🛍️
Duck Typing in Python - Writing Flexible and Decoupled Code🦆
Dive in, and let me know what you think about this issue in today’s survey!
Stay awesome!
Divya Anne Selvaraj
Editor-in-Chief
🐍 Python in the Tech 💻 Jungle 🌳
🗞️News
Exclusive to Gemini Advanced - Edit and run Python code: Gemini Advanced has introduced a ChatGPT-like Python Interpreter for paid users, enabling code editing and execution within its interface for $20/month. Read to learn more.
Pydantic 2.6.3 released: This new version of the leading data validation library for Python updates pydantic-settings in the docs and fixes a schema generation bug for discriminated unions.
💼Case Studies and Experiments🔬
Developing Python for Google Sheets - Traps and tricks: This case study details Neptyne's journey in integrating Python with Google Sheets, including challenges faced and solutions created. Read to learn about innovative solutions for integrating Python functionalities within Google Sheets while overcoming platform limitations.
📊Analysis
Bash-Script vs. Stored Procedure vs. Traditional ETL Tools vs. Python-Script: This live chapter compares traditional and modern data orchestration methods and explores their evolution, core concepts, and how they cater to data engineering needs. Read for insights into the adaptability and efficiency of Python in modern data engineering.
The most important Python news from 2023: This website serves as a curated guide to last year's most significant Python news, developments, projects, themes, and underdog resources worth your attention. Read to catch up on what you may have missed.
🎓 Tutorials and Guides 🤓
Duck Typing in Python - Writing Flexible and Decoupled Code: Duck typing in Python focuses on object behaviors and interfaces rather than their types. Read to learn how to implement this approach in Python to write more adaptable and maintainable code.
Building an E-commerce Product Recommendation System with OpenAI Embeddings in Python: This tutorial explains the concept of embeddings, their importance, and walks you through developing a system with Python, utilizing OpenAI's API and Kaggle's product datasets. Read to enhance your understanding of ML applications in e-commerce.
Web Scraping in Python - The Complete Guide: This article provides a comprehensive guide on building robust crawlers with libraries like BeautifulSoup. Read to learn how to address common challenges and utilize best practices to build scalable and efficient web scrapers.
Pagination in Python: how to scrape a paginated website: This resource covers the concept of pagination, types of pagination, and a step-by-step tutorial on scraping a demo website that uses 'next' buttons for pagination. Read to enhance your web scraping skills and learn how to deploy scalable scrapers in the cloud.
Continuously fuzzing Python C extensions: This article introduces you to Google's Atheris, a coverage-guided fuzzer capable of testing both pure Python code and Python C extensions. Read to learn how to set up fuzzing environments, integrate with OSS-Fuzz for continuous fuzzing, and leverage CIFuzz for immediate feedback on commits.
Multi-tenant todo list app with Nile, Python, FastAPI and SqlAlchemy: This guide covers database setup, table creation, environment configuration, and running the app, including REST API usage for todo list management. Read to discover practical steps from setup to deployment.
🔑 Best Practices and Code Optimization 🔏
Neat parallel output in Python: This article introduces a method utilizing multiprocessing and terminal manipulation techniques to ensure clean, readable output for parallel processing tasks. Read to be able to achieve efficient and orderly display of parallel process outputs for tasks requiring concurrent execution.
Python Dependencies Are Fixable: This article demonstrates how using virtual environments, pip freeze, and pip-tools for secure dependency locking can enable you to effectively manage Python projects. Read to learn how to adopt better default settings for improved project management and security.
How to control package versions in your Python project: Poetry is a Python dependency management tool that supports specifying version constraints and streamlines workflows for both individuals and teams. Read to learn how you can use this tool to simplify version control and resolve dependencies efficiently.
Remote memory profiling with Memray: Memray, a Python memory profiler developed by Bloomberg, identifies memory leaks down to the C level and has a new Textual interface for monitoring processes in the terminal. Read to learn how to use Memray to enhance you optimization and debugging practices.
How to spend less time writing Django tests: This article introduces Kolo, a tool for auto-generating Django integration tests, emphasizing how it can streamline the test-writing process. Read to learn how to improve productivity and code quality without the usual tedium associated with writing tests manually.
Take the Survey, Make a resource request!
🧠 Expert insight 📚
Here’s an excerpt from “Chapter 13: Creating a Secure Login and Signup Process for Web Applications” in the book, Web App Development Made Simple with Streamlit by Rosario Moscato, published in February 2024.
What is SHA-256 and why should we use it?
SHA-256 is a cryptographic hash function that produces a 256-bit hash value from a data input. It is part of the SHA-2 family of hash functions that were designed by the National Security Agency (NSA)
and published by the National Institute of Standards and Technology (NIST) in 2001.
SHA-256 is a widely used hash function for a variety of applications, including the following:
Password storage: SHA-256 is used to store passwords securely. When a user creates an account on a website or application, their password is converted into an SHA-256 hash and stored in the database. When the user logs in, their password is converted into an SHA-256 hash and compared to the hash stored in the database. If the two hashes match, then the user is successfully logged in.
Digital signatures: SHA-256 can be used to create digital signatures. A digital signature is a cryptographic technique that allows the sender of a message to verify their identity and the integrity of the message. To create a digital signature, the sender calculates the SHA-256 hash of the message and then encrypts the hash with their private key. The sender then sends the message and the encrypted hash to the recipient. The recipient calculates the SHA-256 hash of the message and then decrypts the encrypted hash with the sender’s public key. If the two hashes match, then the recipient can be sure that the message is authentic and has not been tampered with.
File integrity verification: SHA-256 can be used to verify the integrity of files. To do this, the SHA-256 hash of the file is calculated and then stored. When the file is needed, the SHA-256 hash of the file is calculated again and compared to the stored hash. If the two hashes match, then the file is known to be intact.
SHA-256 is considered to be a very secure hash function. It is resistant to collision attacks, meaning that it is very difficult to find two different inputs that produce the same hash value. It is also resistant to preimage attacks, meaning that it is very difficult to find the input that produces a given hash value.
Here are some reasons why you should use SHA-256:
It is a very secure hash function
It is widely used and supported
It is relatively easy to implement
It is free to use
If you need a secure way to store passwords, create digital signatures, or verify the integrity of files, then SHA-256 is a good choice.
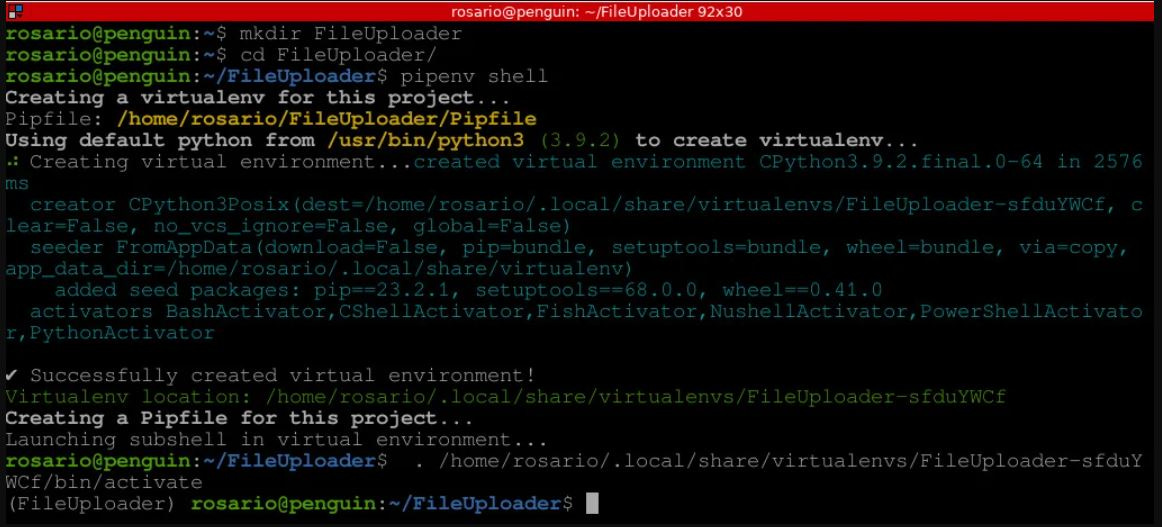
Now that we have all the information we need, let’s start coding. As usual, we have to follow some typical steps to set up a new virtual environment:
Create a new directory named Login_Skeleton.
Enter this directory and write pipenv shell to create a new virtual environment.
Install the streamlit and pillow packages.
Create a new empty Python file named app.py.
Launch your IDE (Sublime Text).
Figure 13.1 shows all these steps, from creating the new directory to installing the required libraries:
Figure 13.1: Virtual environment and app.py file preparation
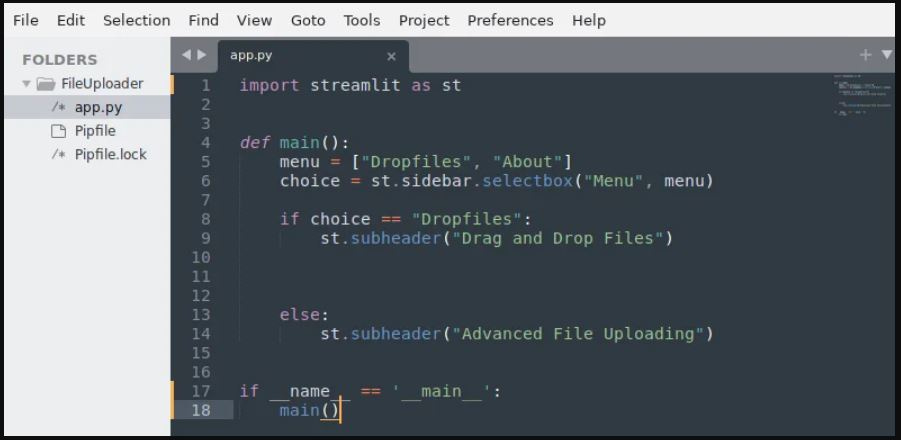
Now, we are ready to edit the Python code in the app.py file.
Inside Sublime Text, we can start writing the code for our new login/signup web app, as shown in Figure 13.2:
Figure 13.2: Starting code
The preceding code should be quite familiar. Here’s a breakdown of what we did:
At the very beginning, on lines 1 and 2, we import the necessary libraries – in this case, streamlit and Pillow.
After that, on line 5, we create a main() function:
In the main() function, we write some HTML code in the html_temp variable (line 8) to set a big title in the web app that specifies the background color, the padding, and the text color
Then, we visualize the HTML code using the st.markdown instruction (line 14)
Next, we create a list on line 16 that contains the voices of the menu we want to visualize and add a selectbox in the sidebar on the left-hand side of the screen.
Then, we check the selection (line 19) and if it is Home, we do something: at the moment, we just write some text in the subheader format. Meanwhile, if the selection is Login (line 25), we pass (we will develop the code for this in the Creating the Login menu subsection); the same goes for Signup (line 28).
Finally, we add an About section (line 32), where we are free to write anything we want.
Please note that in the Home section, just after the header, we can visualize an image thanks to the st.image instruction. This image, named login.png, must be present in the same directory as the app.py file, as shown in the Folder section of the editor in Figure 13.2.
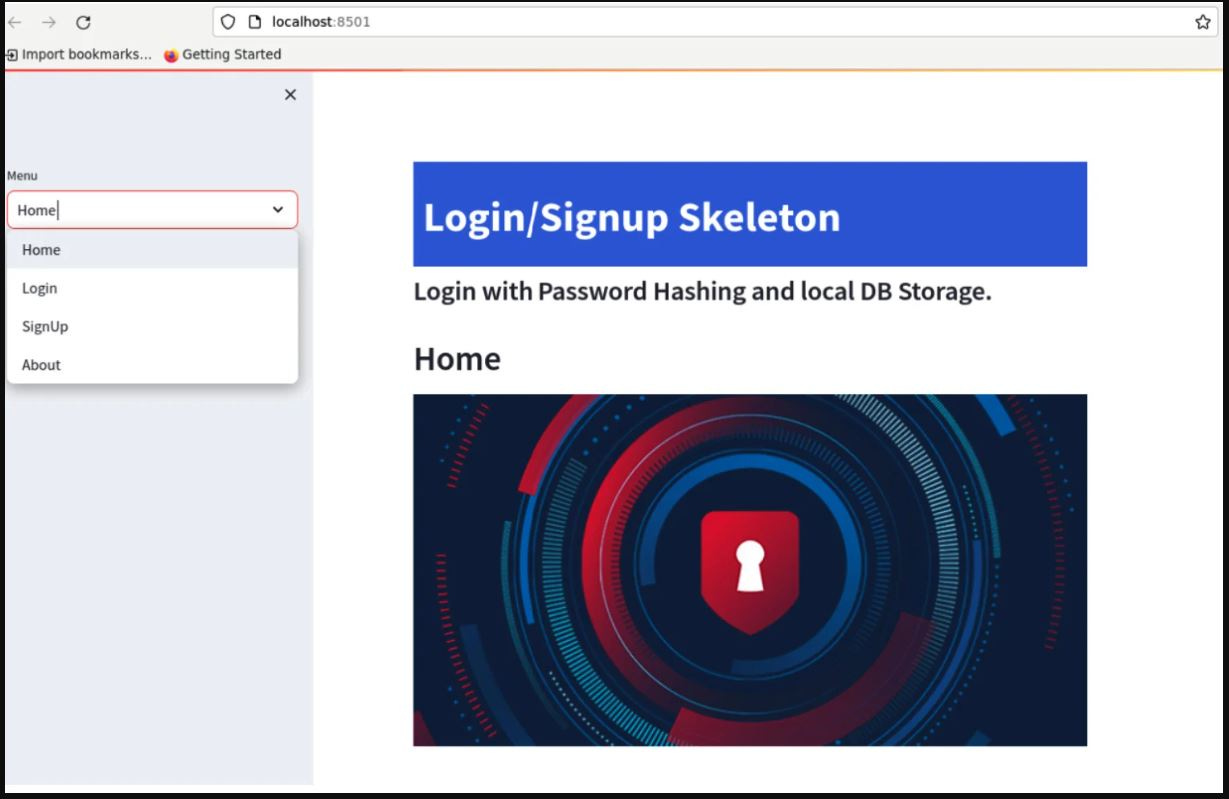
As usual, when we execute the following command, the web application will be executed:
pipenv run streamlit run app.py
The result in the browser is quite simple and clean:
Figure 13.3: The login/signup web app in the browser
On the left, we have the sidebar with the menu, while in the middle, there is the Home section with a beautiful picture.
The skeleton is ready. Now, it’s time to connect our web app to a database so that we can save all username/password data and use it at the proper time.
Packt subscribers can continue reading for free here. You can buy Web App Development Made Simple with Streamlit by Rosario Moscato here!
And that’s a wrap.
We have an entire range of newsletters with focused content for tech pros. Subscribe to the ones you find the most useful here. The complete PythonPro archives can be found here.
If you have any suggestions or feedback, or would like us to find you a Python learning resource on a particular subject, take the survey or leave a comment below!